%20(9).png)
2021: Another Record-Breaking Year for Cybersecurity Attacks
Is today’s security monitoring approach effective enough to deal with upcoming and existing cyber threats? The answer is, probably not. Each year, we have seen an increased number of cyber-attacks, and 2021 was no different. New data suggests that our current security monitoring approach is ineffective and that many organizations are at risk, even when they have a strong perimeter defense. In this blog, we explore the most recent data on cyber-attacks, if the traditional security monitoring approach is still relevant, and what you can do to protect your organization.
Download the Network and Security Monitoring Infrastructure is Complex and Incomplete Infographic
Cyber-Attacks Are on the Rise
When it comes to cyber-attacks, 2021 was a banner year. In fact, it was an all-timer. North America had an average of 503 weekly attacks per organization, which was a 61% increase over 2020, with the highest average cost of damages in over 17 years. In a Checkpoint Research global study published in January 2022, Checkpoint documented a year-over-year increase of 50% per week in attacks on corporate networks globally, and almost as much on government and military organizations. Intellectual property software vendors, education, and research facilities were prime targets, with the highest increases across all industry verticals.
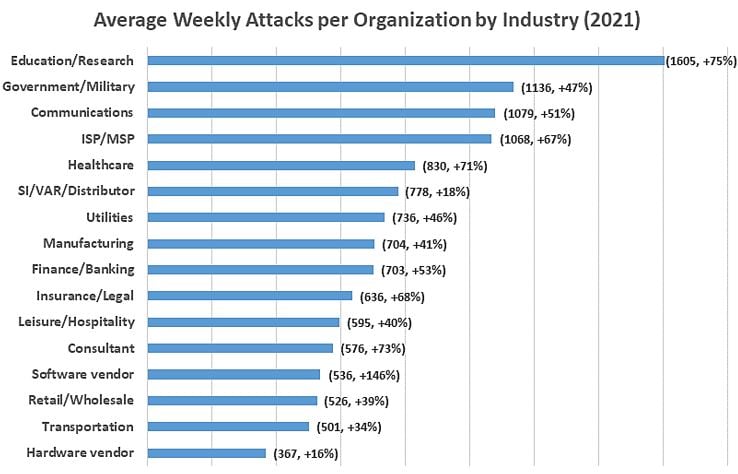
Check Point Research Jan 2022
Source: Check Point Research: Cyber Attacks Increased 50% Year over Year - Check Point Software
But unlike a few years ago, hackers are now much better prepared, carefully selecting their targets and improving their assessments of environments into which they deploy their malware and carry out attacks. These attackers use Advanced Persistent Threats (APT) to steal information over a long period of time, rather than infiltrating the network and leaving quickly after. Once again, organized crime continues to be the number one threat. Financially motivated, they have resources most victims have a hard time matching. IBM Security, in its “2021 Cost of a Data Breach Report,” shows that it can take 212 days from compromise to detection for the average attack, which slows down an organization's incident response. That means a total of seven months of exploration by the threat actors until they are discovered, significantly maximizing their impact. Over the last few years, in many of the large scale operations -- often called multi-vector attacks -- threat actors assault at all fronts. They exploit the mobile devices, then move to other end-devices to obtain additional credentials, and then explore how to access and steal valuable assets. IBM states that threat actors breach between 2,000 – 101,000 records during this timeframe.
.png?width=872&name=Images%20for%20Pillar%20Page%20Blogs%20(1).png)
*2021 Cost of a Data Breach Report – IBM Security
**2019 CISO Benchmark Study - Cisco
And the damage from an attack now even goes beyond lost or encrypted data files. Mandiant identified a new iteration of ransomware attacks: ‘Multifaceted extortion’ not only encrypts victims’ valuable data, but they threaten their victims with publishing sensitive information or selling them to third parties. This means that in addition to the productivity and infrastructure damage, organizations now need to consider reputational damage, loss of competitive advantage, regulatory fines, and class action lawsuits. According to IBM, US companies experience an average of $9 million in damages for each breach.
But those damage numbers vary widely. An example is the 2017 Equifax breach which cost Equifax a stunning total of losses of $1.7 billion. And despite having $125 million in cybersecurity insurance coverage at the time of the breach, this hardly covered the total damages.
Is the traditional security monitoring and network monitoring approach still sufficient?
Even though today’s network monitoring and security tools are growing ever more sophisticated and “intelligent”, the primary defenses most organizations use are still based on concepts developed 30 years ago: firewalls, intrusion detection systems (IDS), and endpoint antivirus protection in combination with device information such as logs, events, and other digital forensics. More sophisticated organizations over the last few years also started to use network traffic monitoring at strategic points in their network utilizing network detection and response (NDR) solutions. Even though the information obtained has been significantly enriched and refined, threat actors with access to vast resources, have had plenty of time to evolve their attack approaches to circumvent those defenses.
Firewalls, intrusion detection and prevention systems (IDPS), and endpoint protection products are still the most common tools to detect and keep threat actors out. However, this concept is based on the outdated assumption of trusted vs. untrusted networks: your managed network on the inside of your organization being trusted and known, the outside world being untrusted.
.png?width=934&name=Images%20for%20Pillar%20Page%20Blogs%20(2).png) Intrusion detection technology has certainly evolved from pattern matching to stateful protocol tracking and application aware analysis, with specialized application-specific firewalls such as web application firewalls (WAFs) and email security gateways. More sophisticated vendors have embraced user and entity behavior analytics (UEBA), matching protocol and application behavior analysis with the identity of the device and user. This allows for a more fine-grained analysis, identifying the use of “unusual applications” on a device or communicating with previously unused destinations, which may indicate misuse. NetFlow became an important source for this approach, providing device-specific traffic information and visibility beyond the network and end-point perimeter, generated by various devices along the network path.
Intrusion detection technology has certainly evolved from pattern matching to stateful protocol tracking and application aware analysis, with specialized application-specific firewalls such as web application firewalls (WAFs) and email security gateways. More sophisticated vendors have embraced user and entity behavior analytics (UEBA), matching protocol and application behavior analysis with the identity of the device and user. This allows for a more fine-grained analysis, identifying the use of “unusual applications” on a device or communicating with previously unused destinations, which may indicate misuse. NetFlow became an important source for this approach, providing device-specific traffic information and visibility beyond the network and end-point perimeter, generated by various devices along the network path.
But despite all of these advances in cyber threat intelligence, threat actors are still making it into our networks. As the FireEye CEO Kevin Mandia stated during a March 2021 US Senate Intelligence Committee hearing on the Solar Winds attack on whether properly configured firewalls are effective in thwarting threat actors, he said: “We do over 600 ‘red teams’ a year. Firewalls never stopped one of them.” As attack methods are constantly evolving, perimeter defense needs to be diligently updated. Unfortunately, they still struggle with detecting Zero Day attacks, credential thieves, and malicious insiders.
Zero Trust to the Rescue?
The concept of Zero Trust is trying to address network detection and response issues and by constantly validating any action an endpoint is taking in the network and considering even the internal network a “hostile” environment. However, this requires significant changes across the entire application delivery chain and will take years (if not decades) to implement. The question is what can be done in the meantime?
At Axellio, we believe in three fundamental principles to help improve your security posture:
- Accept the fact that internal threats are real – and monitor for it.
- Move beyond perimeter defense
- Go beyond meta data (logs, events, flows) to quickly assess, triage, and mitigate threats
In our next blog we will explore each one of those areas in detail and how you can improve your threat hunting and threat detection efforts across your organization.
